Written by: Miguel Ángel Blanco López
"El vivo vive del bobo" - Popular adage.
We have all at some point in our lives heard the popular saying quoted above, and I hope you are not offended. I know there are no "pacifiers" here, but there is a lot of naivety, and for the topic I will talk about it fits perfectly.
In this era, we enjoy great facilities thanks to technology. Most likely, many of the activities you used to do in person are now done through a web platform or an application on your cell phone. A large percentage of people now perform tasks such as bill payments, bank transfers, and even purchases, just to mention a few, mediated by information technologies.
But... Are you sure that the website where you are about to enter your banking credentials is really the website of your bank? Are you sure that the platform where you are going to pay your utility bill is the one provided by the collecting agency? Are you sure that the store where I just shopped is authentic?
All this refers to what is known as social engineering. INCIBE (Instituto Nacional de Ciberseguridad) of Spain defines the concept as a technique used by cybercriminals to gain the trust of a user and get them to do something under their manipulation and deception, such as: execute a malicious program, provide their private passwords, or buy from fraudulent websites.
In my opinion, it all boils down to a scam that simply takes advantage of people's naivety and their few precautionary measures on the net. Generally, advanced computer knowledge is not required to perform a social engineering attack. As you can see, social engineering attacks do not always require password cracking or infecting devices with viruses; in social engineering attacks, we give all our valuable information to the attacker ourselves.
Common social engineering attacks:
Vishing: This technique consists of contacting the victim via phone call, impersonating a trusted entity or person, and thus manipulating the target to reveal personal information or perform actions that compromise their security and that of the computer systems and/or devices to which they have access. Be very careful the next time you are called to tell you that you are a beneficiary of some government program, or when a supposed police patrolman calls you saying that your brother ran over someone and that they are going to give you directions to "collaborate" with him, because it is most likely an attempt to defraud or "collaborate" with him, because it is most likely an attempt to defraud you. vishing.
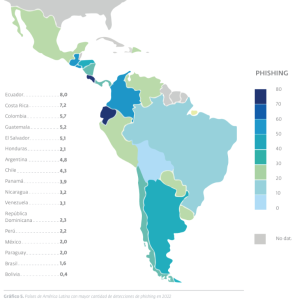 Phishing: Have you ever received a text message from Amazon's manager himself with a job offer? Or maybe you received an email notifying you that your password was blocked or that your payment methods were rejected? Well, this is what is known as phishingA social engineering technique that seeks to obtain personal information from its victim by impersonating a trusted entity or person using text messages, emails and even by impersonating web pages.
Phishing: Have you ever received a text message from Amazon's manager himself with a job offer? Or maybe you received an email notifying you that your password was blocked or that your payment methods were rejected? Well, this is what is known as phishingA social engineering technique that seeks to obtain personal information from its victim by impersonating a trusted entity or person using text messages, emails and even by impersonating web pages.
According to ESET's security report for Latin America (2023), the Latin American countries with the highest percentage of phishing detection are: Ecuador 8.0%, Costa Rica 7.2% and Colombia 5.7%. Note that Colombia is in third place, hence the importance of being very careful and pay attention to the information we deliver by the various media.
How to protect yourself?
It is important to clarify that in the field of computer security no method or system is infallible: however, most of these types of attacks will fail if we are stricter with our security measures.
To prevent becoming a victim of social engineering attacks, the computer security company Kaspersky recommends:
- Change your passwords frequently.
- Enable multifactor authentication whenever available.
- Always type the web address you want to visit, do not do it through the search engine results.
- Do not expose your personal and/or family information.
- Do not allow strangers to connect to your main wifi network.
- Do not leave your devices unprotected in public.
- Use VPN (if available).
Additionally, I would like to share my personal security socks, because as I mentioned before, it is not only through an application or technological device that our information can be stolen:
- Don't be lazy: Close sessions of applications you are not using, avoid using autocomplete of web browsers, destroy information that is no longer relevant to you.
- Pay attention to details: In the emails and text messages you receive, always validate the senders, analyze the coherence of the content and avoid leaving sensitive information in any web form.
- Always validate the environment and context: If you are in a public place be careful what you say, you do not know who may be next to you. If you receive calls from unknown numbers, pay special attention to the sounds you hear in the background and the way the caller expresses himself.
- Be wary of everything and everyone: Always question who is asking for what information and why. Before posting that selfie or picture of the walk you like so much on your favorite social network, check that nothing that should not be exposed in it (valuables, location, other people, among others). And avoid having valuable information in view.
- Avoid using public or open networks.
- Check what you throw away: Someone interested may know a lot about you if they check your trash can The item you bought from an online store and received at your home comes with the carrier's tracking document. Before discarding it, make sure that the information contained in it is irretrievable. Remember that one man's trash is another man's treasure.
- Work on controlling your emotionsTry to always remain calm and composed when making important decisions, as attackers will often seek to generate panic and take advantage of your vulnerable state.
As you have seen, social engineering attacks are very common and are on the rise year after year. They are usually the gateway to higher impact attacks. For this reason we must be very careful and reserved with the information we give out. If you take care of your information, you are taking care of your whole social circle, since you may not fall into these scams, but through you they can reach a family member, a friend, a co-worker, and maybe this person will be successfully attacked.
Sources:
- Social Engineering - INCIBE
- ESET Security Report Latin America 2023.
- The ABC of computer security, a practical guide to understand digital security. Computer security for dummies - Oscar Arango Gómez.
- What is social engineering?
